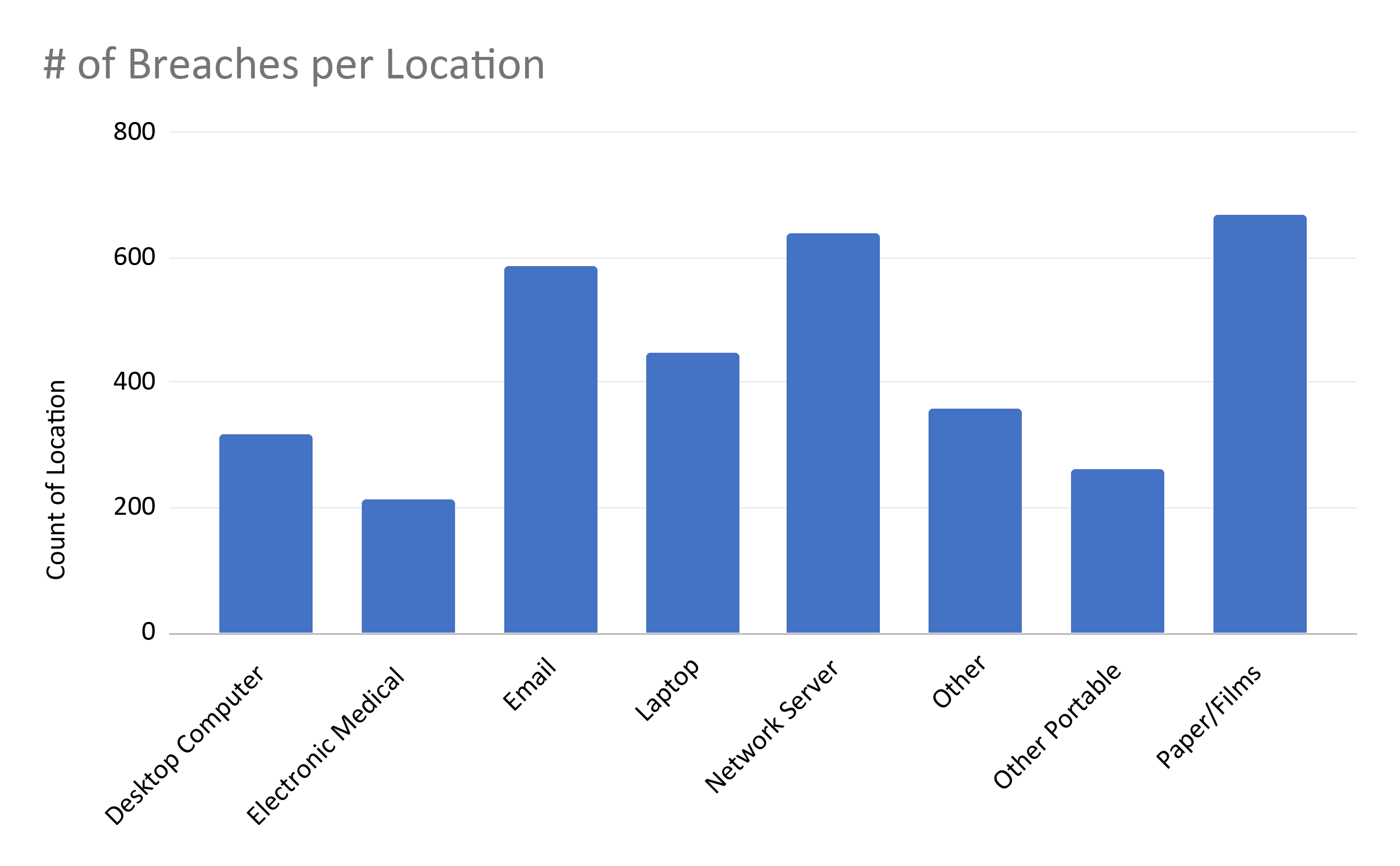
Yesterday we talked about breaches from the perspective of the type of breach. Another dimension is the location of the data. Over the last 10 years, patient health information (PHI) has transitioned from paper files to servers and clouds. This is reflected in the breach reports.
In the first chart, we see that paper/films is the top location for data breaches, followed by network server and email. It is notable that if we combine physical electronic devices (desktop computers, laptops, other portable devices) into one category, it becomes the top category.
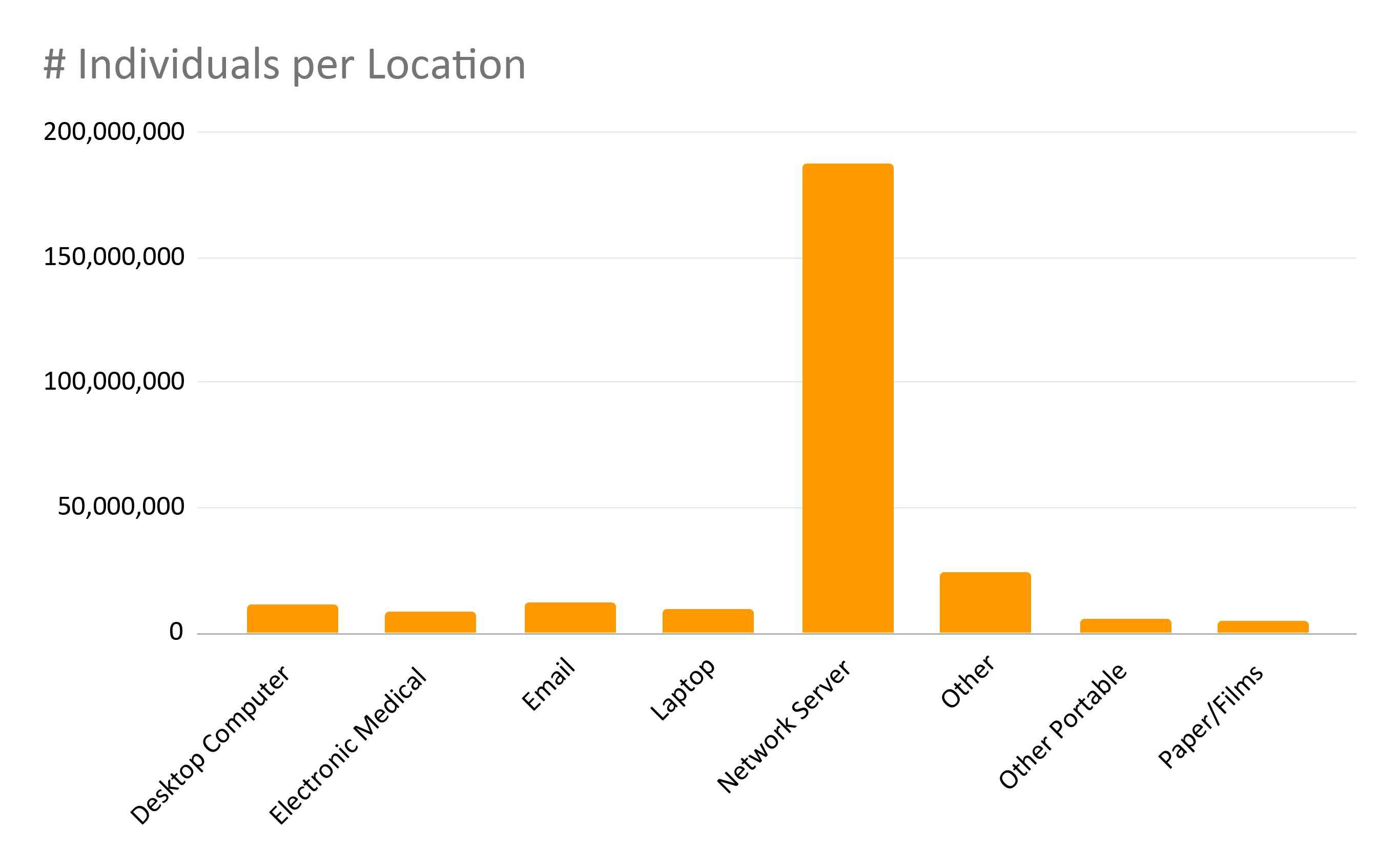
The number of individuals affected per location tells a different story. Network servers are by far the location with the most PHI being breached. The number approaches 200 million individuals affected over the last 10 years.
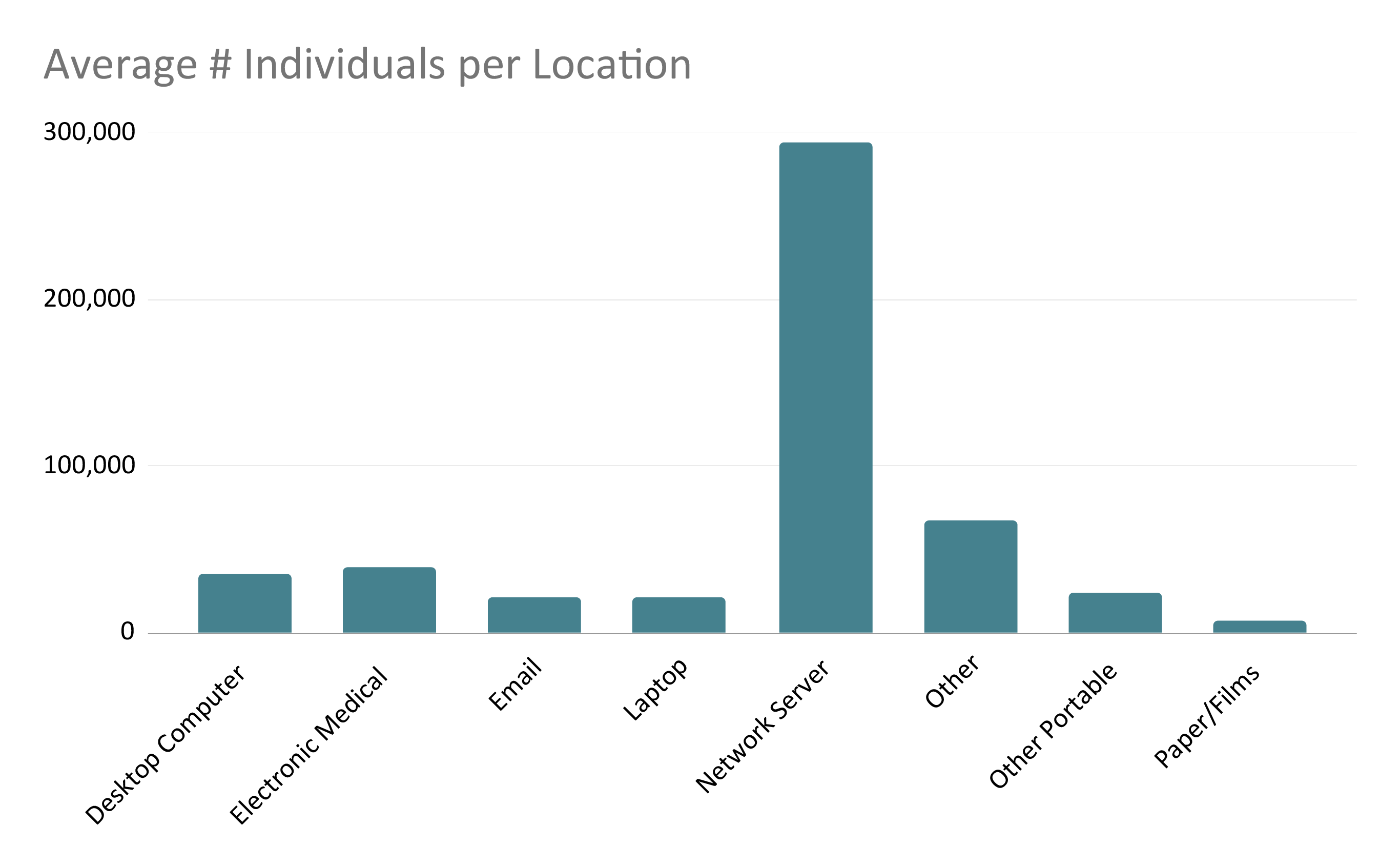
It is not surprising after looking at the last two graphs that the average number of individuals affected per breach is highest in network servers. Contrast that with paper/films with a far lower average. The amount of data that can be obtained in a successful server hack could amount to truckloads of stolen paper records.
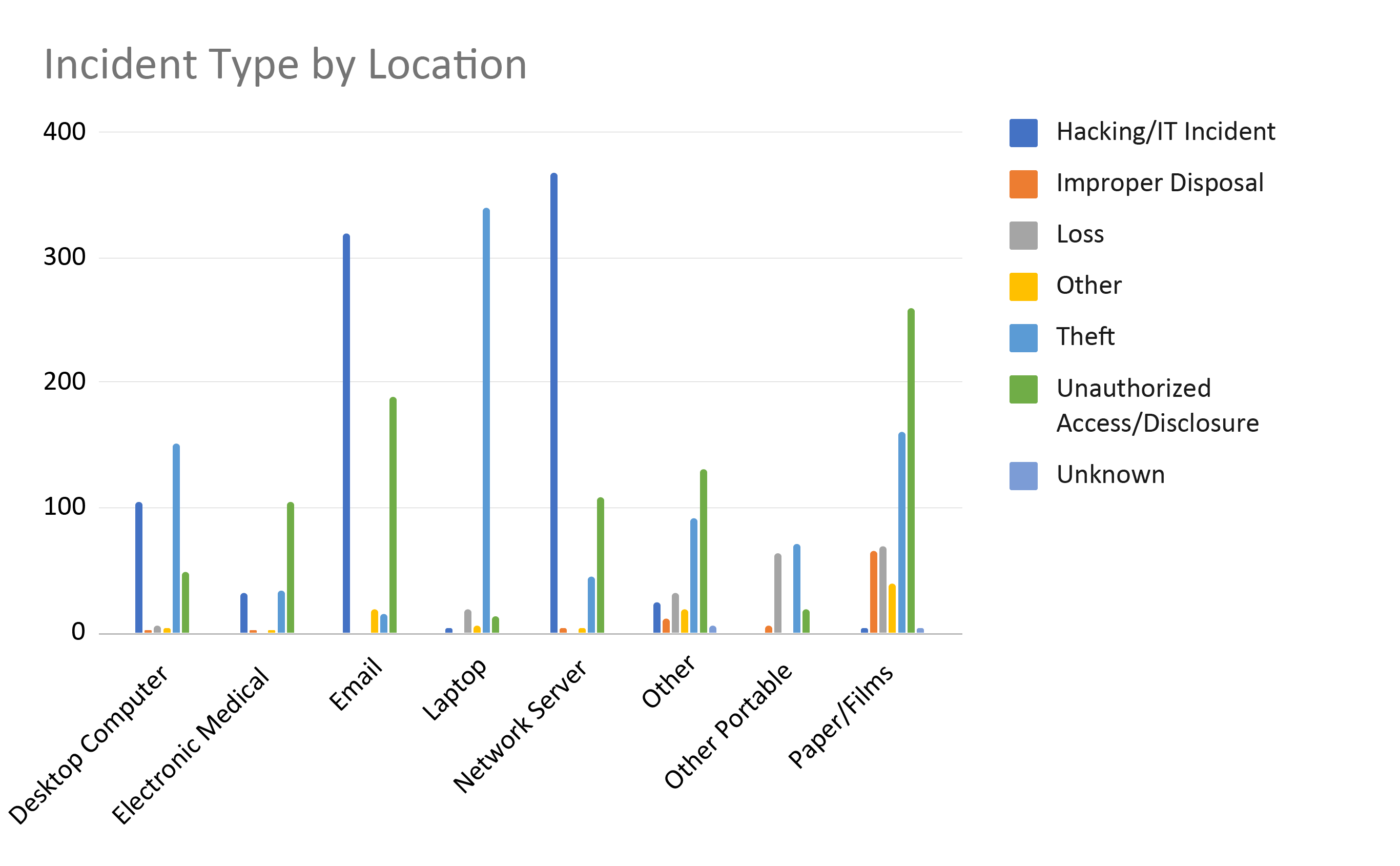
The data becomes even more interesting when we combine the location of the PHI with the types of breaches we discussed in the last post. Most incidents are hacking of network servers. This is where the biggest payoff of data lies. Hacking through email is another common data breach. It seems like phishing attacks are a daily occurrence in healthcare now. Theft of laptops also occurs in high numbers. Reading through individual breach reports, we see many that are laptops lost through car break-ins.
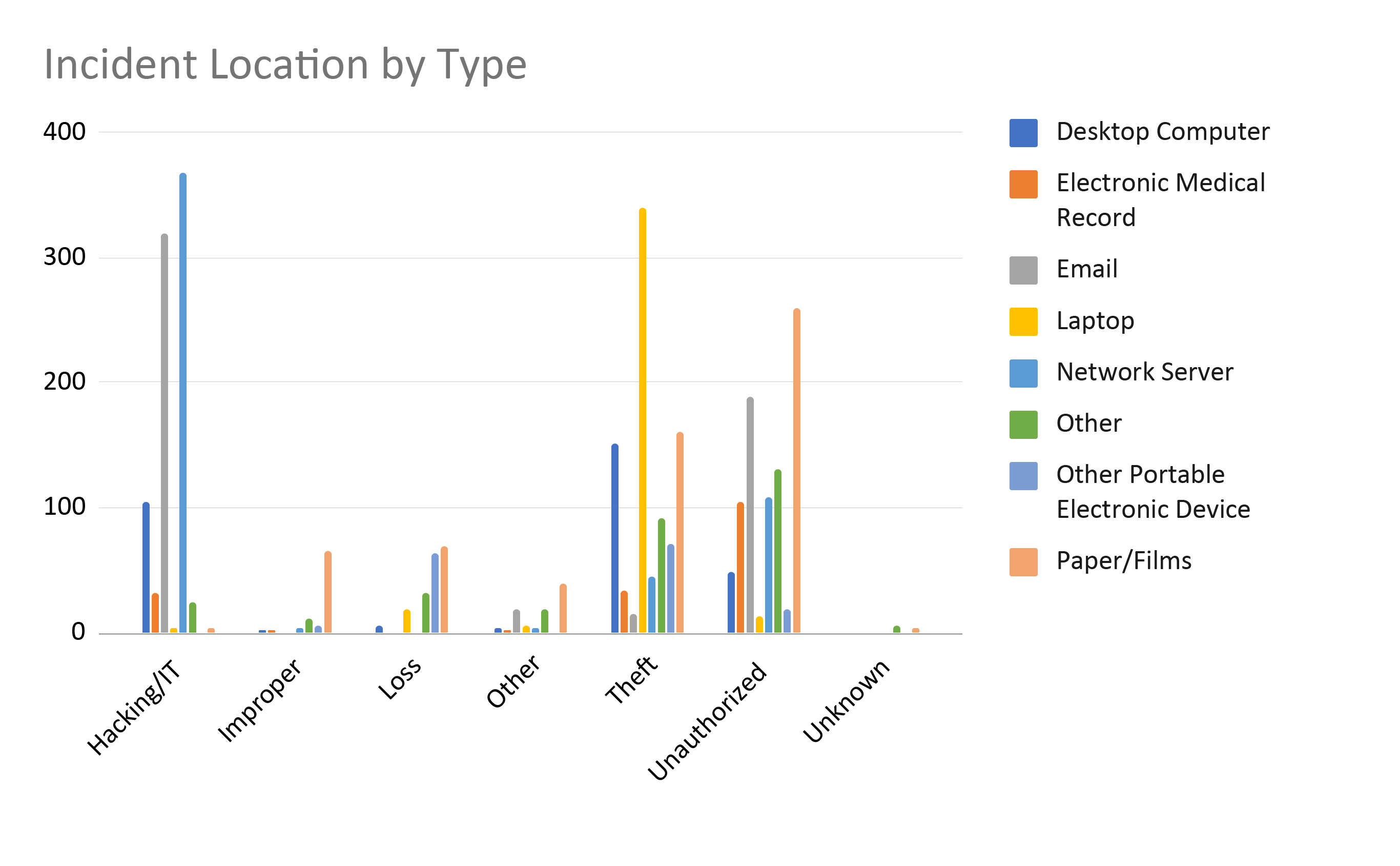
This is another perspective of the same data. Paper/films stand out as being affected by a variety of breach types, except, of course, hacking/IT. As PHI has transferred from paper to EHRs some breaches occur from improper disposal and loss.
The data shows many situations where a breach can occur. Analysis can highlight which vulnerabilities should be prioritized to protect patient data. In the next post, we will look at how the different types of breaches have trended over time.