We are getting close to finishing up a complete report on data breaches from the last 10 years. We started with a wide view and in our last few posts, we took a more focused view of the types and locations of breaches. In this post, we will look at the trends of the different types of breaches over time.
The image below is an overall view of the different types of breaches over the last 10 years. The majority of the breaches fall into the categories of hacking/IT, theft, and unauthorized access/disclosure. There are trends happening that show an evolution of the types of breaches as more patient health information becomes digitized.
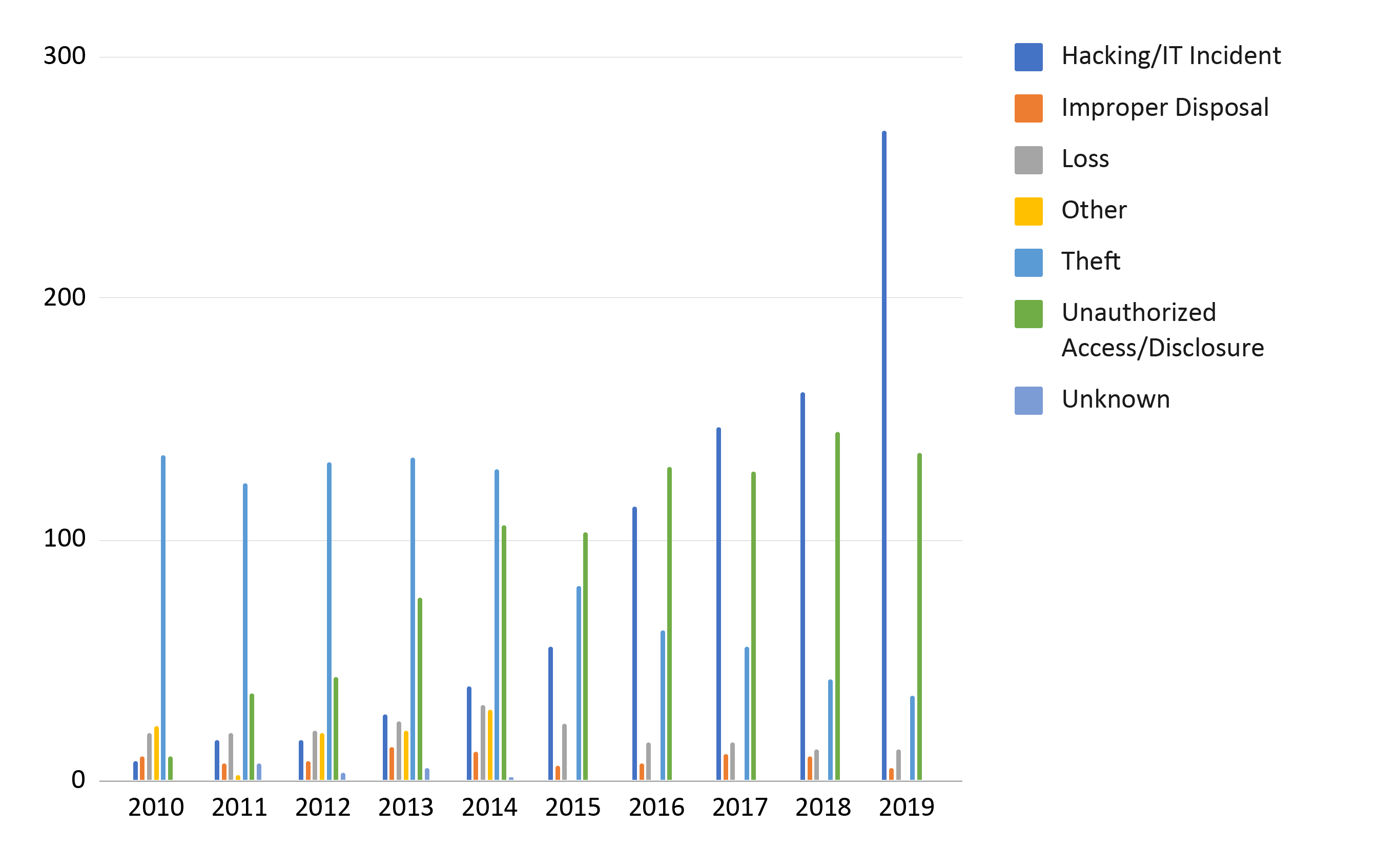
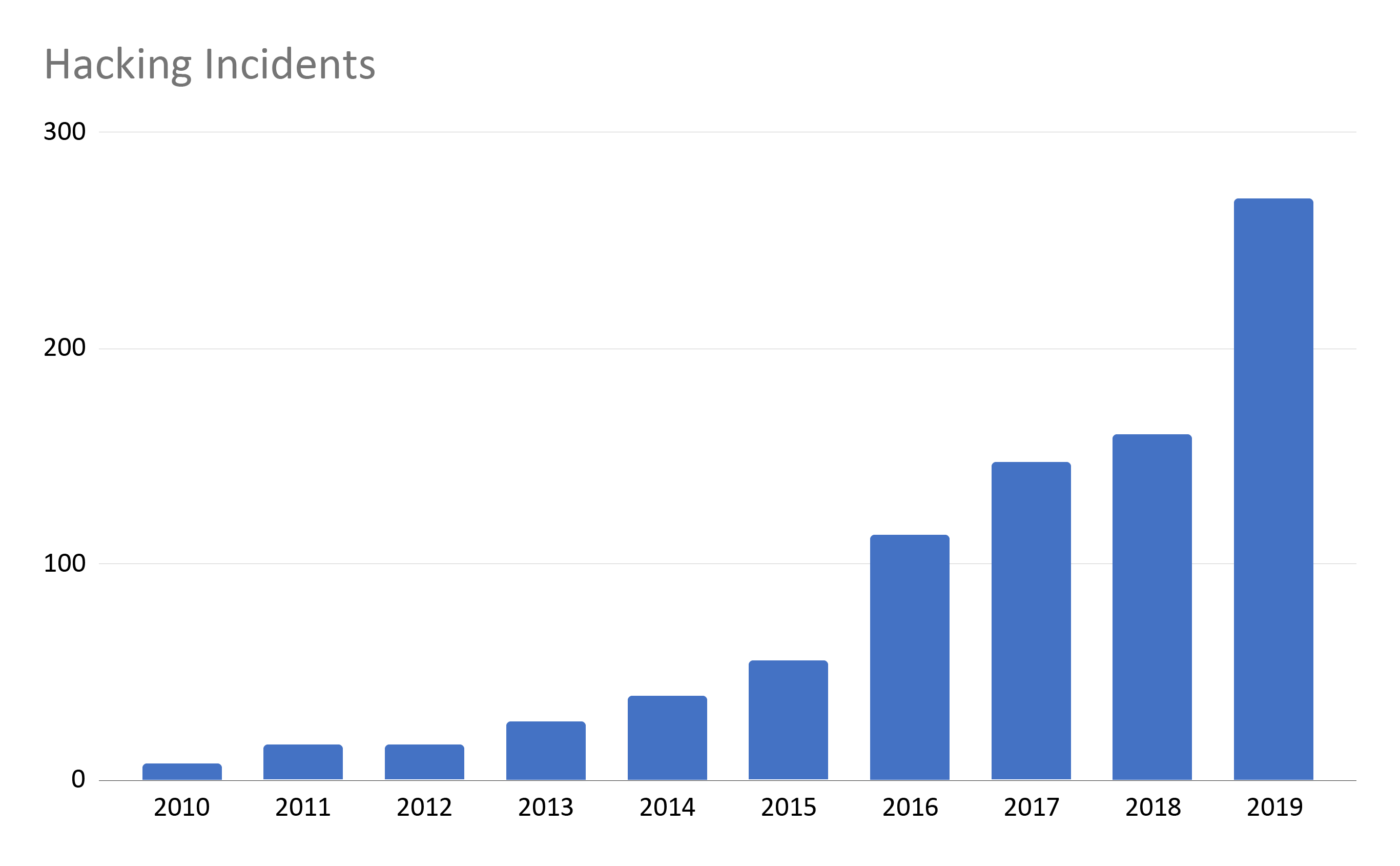
The number of hacking incidents has been growing quickly since the widespread adoption of EHRs began with the HITECH act of 2009. There is a notable increase between 2015 and 2016 where the number doubles from 56 to 114 followed by another significant increase between 2018 and 2019 from 161 to 270.
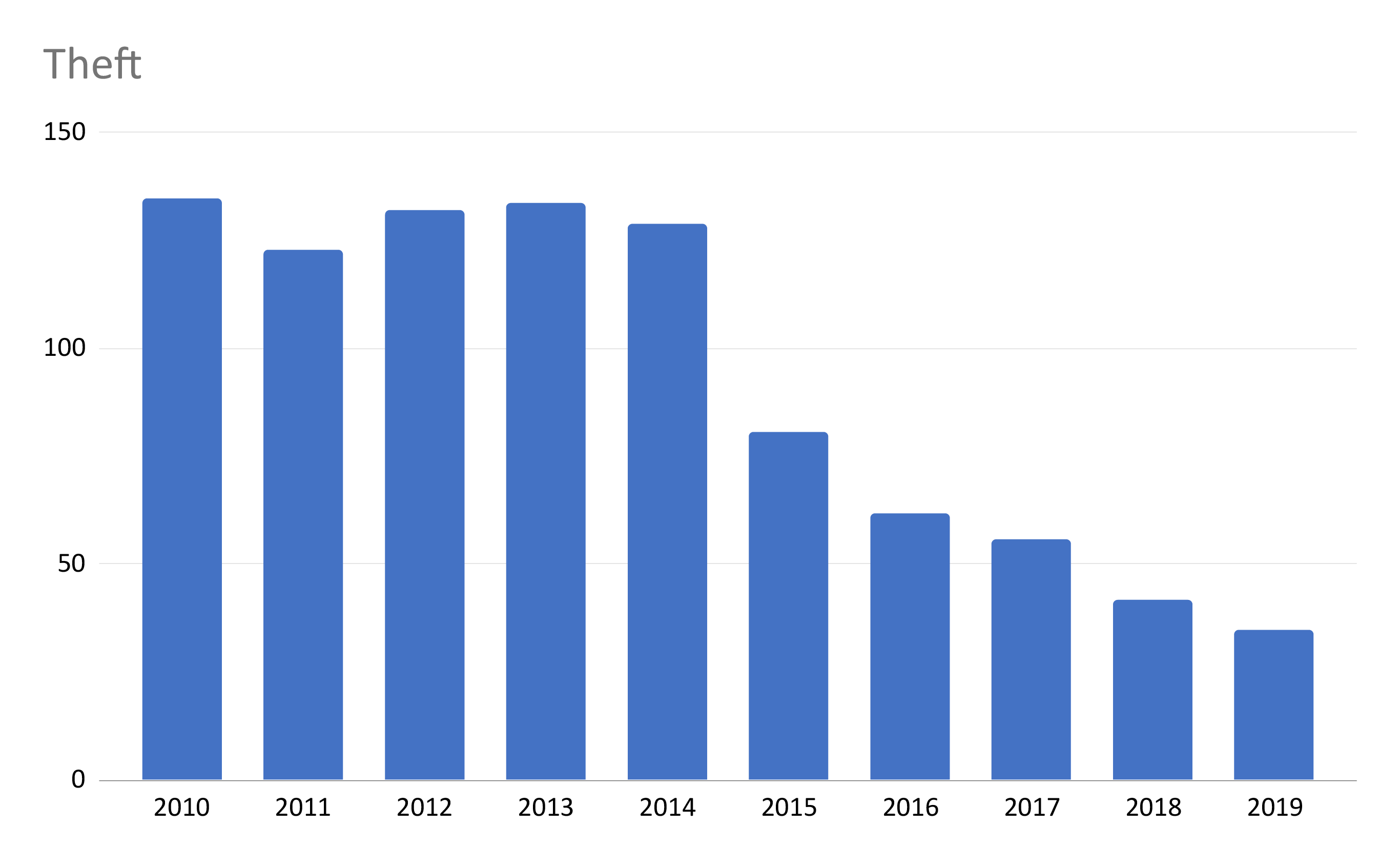
Theft has seen a reduction over time. The analytics we looked at in our last blog also showed theft of laptops was a large source of breaches overall. This is an area we could look deeper into, perhaps comparing the locations of theft over the past 10 years to see if the target media has changed.
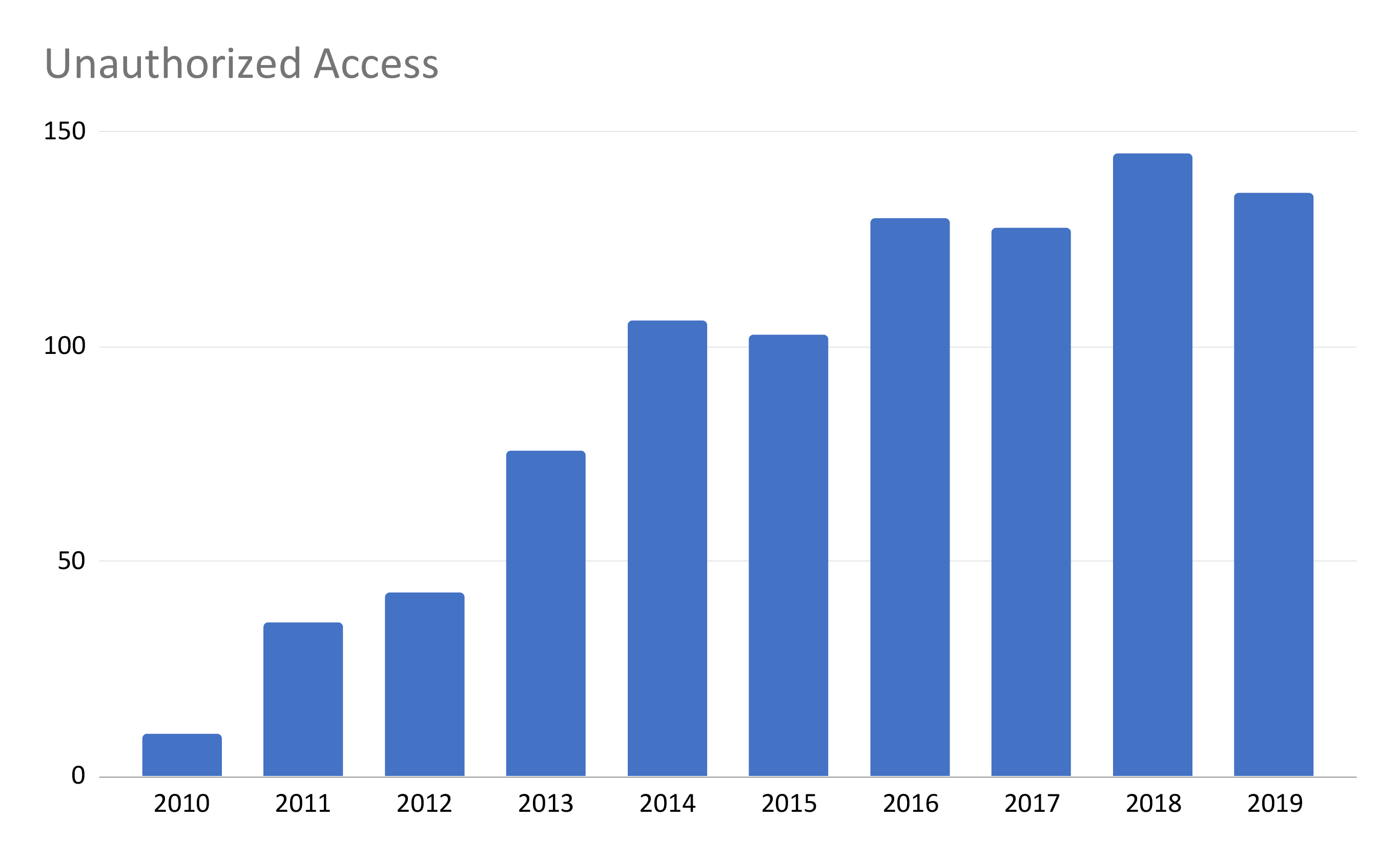
Unauthorized Access/Disclosure has seen a steady rise through time. At the start of our data in 2010, only 10 were reported. In 2019, 136 breaches were caused by unauthorized access/disclosure. This is the largest percentage increase for a type of breach.
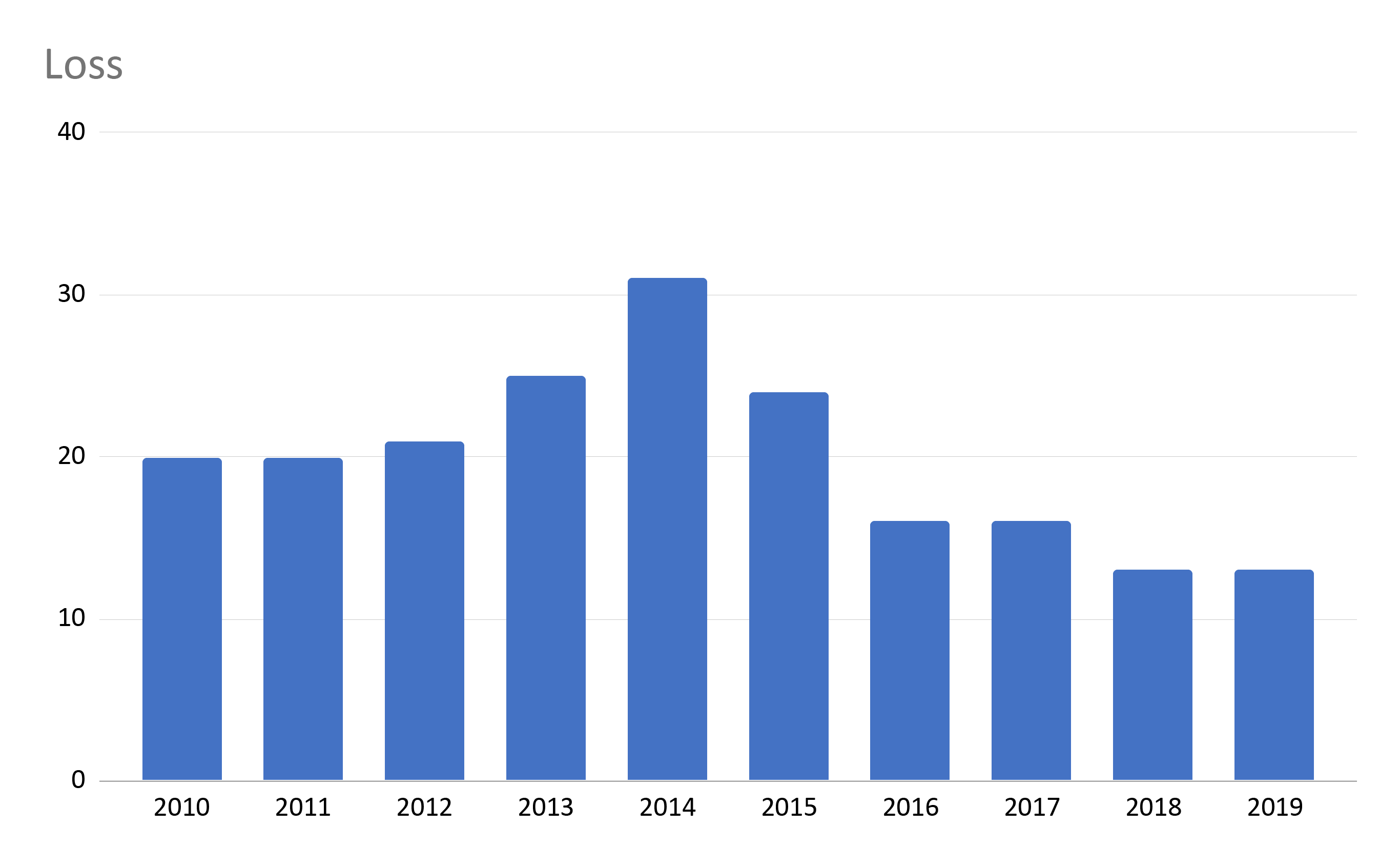
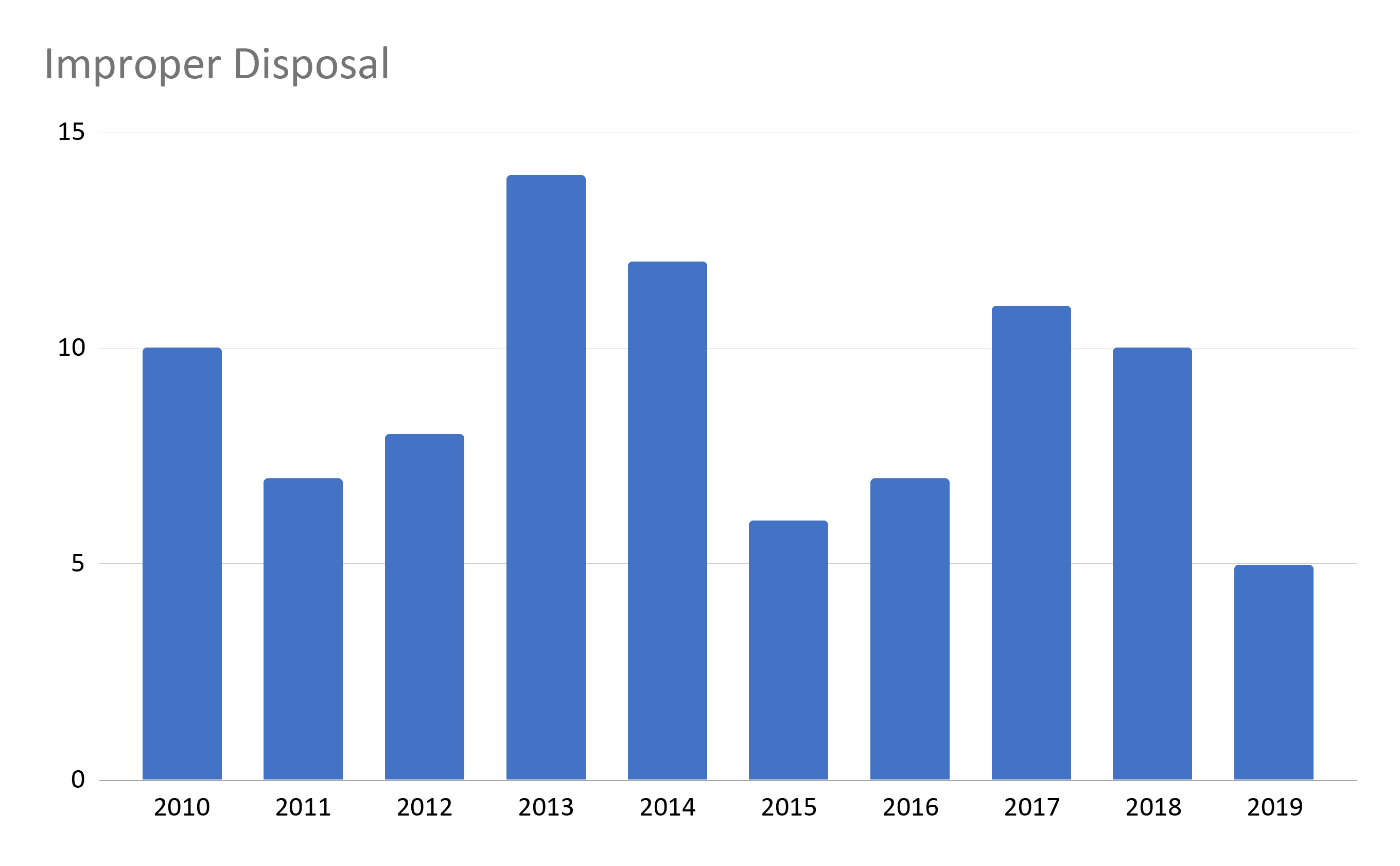
Breaches caused by loss and improper disposal have both remained fairly steady over time. Both had the most incidents in 2013/2014. Although the two causes combined yield far fewer incidents than hacking/IT, theft, and improper access/disclosure, they were still the cause of 18 breaches affecting more than 500 individuals in 2019.
It is interesting to see the trends of breaches as the digitization of PHI took place. Will the trends maintain their trajectory or will we find better ways to protect patient health information?